VictorOps Builds Serverless, Customizable Incident Management Solutions Using Twilio Functions
There are several important variables within the Amazon EKS pricing model. DevOps enhances incident management by promoting a culture of collaboration, automation, and continuous improvement. Relevant channels are like email, mobile apps, self service platforms, etc. Next, follow up items from PagerDuty are sent back into ITSM, including outcomes of the postmortem that need to be prioritized. The tool also includes features for exporting data to Excel or PDF for further analysis. The process responsible for managing the lifecycle of all incidents. Manager Two is responsible for devising and implementing a crisis management training and evaluation programme in conjunction with the Managing Director. Some fixes like bug patches may require further testing even after resolution, to ensure that the issue has been resolved, while others may be quick. Failure of an IT business service affecting a single organization which may include. But, for more complex and/or relatively new incidents, a team of cross functional representatives, known as a swarm, may conduct a joint investigation. Even tech giants are not immune, as their subsidiaries and associated services are affected. The ”WARFIGHTING” SUPERset 7 books. In set up action, first add three Input Data items. Solarwinds starts at $2,995 including the first year of maintenance and offers a downloadable, free 30 day evaluation. Most employers require incident responders to have a bachelor’s degree in cybersecurity, information technology, computer science or a related field, while some companies also offer on the job training. Identification and Logging. Ok, so what’s the bottom line here.

Hello stranger!
Price: Starts at US $9 to $99 with required features and versions increasing. Since incident management focuses on immediate fixes, you should look to resolve issues that will have immediate impacts. They show no hesitation in delegating tasks to anyone. Urgency relates to resolution time, SLA targets, and the criticality of the service. This eliminates time from being wasted and allows you to jump right into identifying concerns and resolving them. Welcome to RSI Security’s blog. System time, current running processes https://postincidentreviews.com/incident-management-sre-tips/ and connecting machines. IT service desks are places for users to submit tickets, chat with the service desk teams, monitor the progress of their tickets, and perform some self service tasks. But since all security events are not equally serious and enterprises simply do not have the resources to aggressively address each and every one incident response requires prioritization. Agencies should instead limit access, as necessary, to specific generative AI services based on specific risk assessments; establish guidelines and limitations on the appropriate use of generative AI; and, with appropriate safeguards in place, provide their personnel and programs with access to secure and reliable generative AI capabilities, at least for the purposes of experimentation and routine tasks that carry a low risk of impacting Americans’ rights. This process involves form customization, which helps personalize forms with the right information and configures fields to suit various departments. Check out out today’s Emergency Management webinar. Try out our quizzes and test your knowledge. Open incidents are monitored until they’re resolved and/or closed. DevOps teams can be comfortable—and successful—with less structured development processes. Annual Revenue: Zoho is a bootstrapped organization and does not reveal this information.
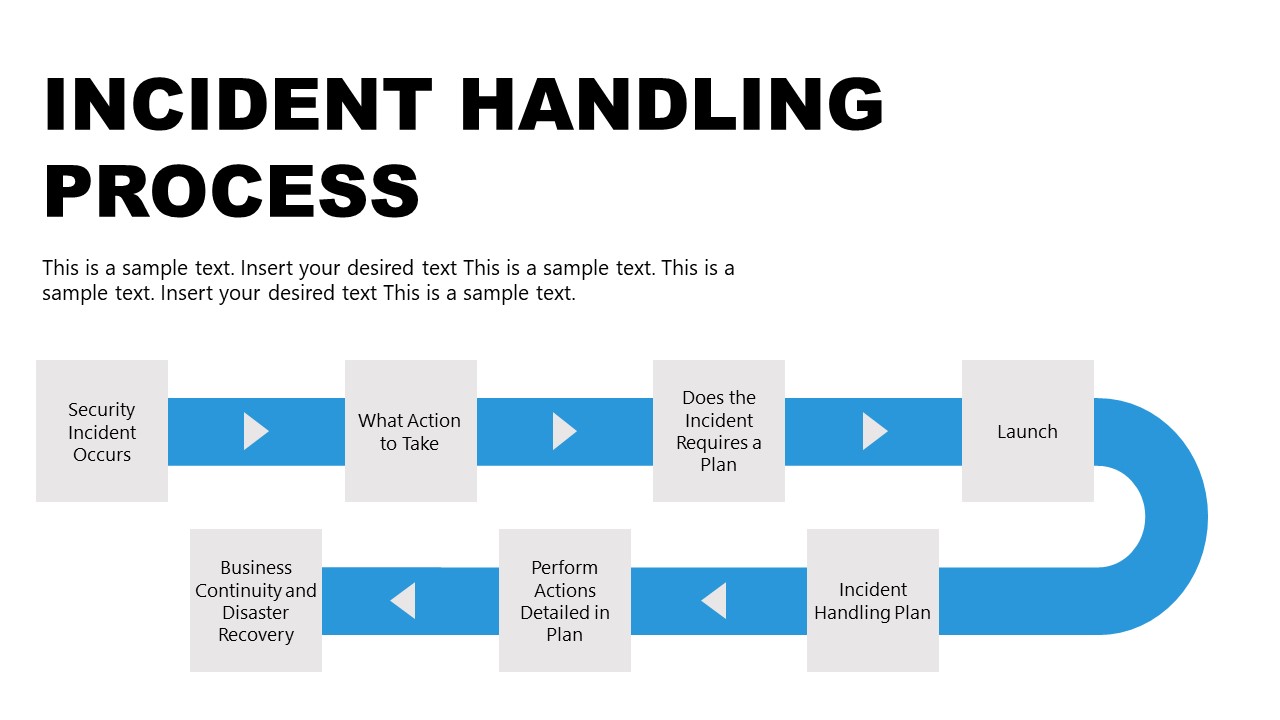
How do incident management and problem management work together?
Set automation to send notifications, update records, and create a change record, to name a few examples. Essentially, reporting an identified incident, or Incident logging is the first step in the Incident management process. An advantage of the “you build it, you run it” approach is that it offers the flexibility agile teams need, but it can also obscure who is responsible for what and when. But, for more complex and/or relatively new incidents, a team of cross functional representatives, known as a swarm, may conduct a joint investigation. Once an incident has been closed, notify users of the incident, how it’s been resolved, and whether or not any additional steps are needed. Support Analyst/ Technical Support. Incident resolution and closure. What are the best credit cards when you are on 5/24 ice. See how your SOC is performing and where you need to evolve your teams and response workflows. Here are a few ways besides reporting incidents that ClickUp can help you with incident management process. An Incident management system or Incident management process aims at reinstating services quickly whereas problem management aims at bringing about a perpetual fix. What Is The Major Incident Procedure.
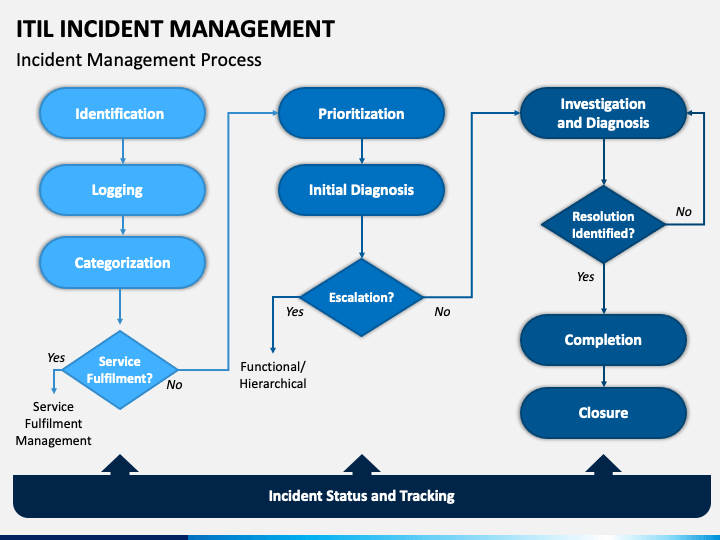
Problem management vs incident management
Learn how to use Jira Service Management’s virtual agent to automate your customer support and save your agents hours every day. Blake logs the incident on their ITSM system, categorizing it as a major incident. If the major incident impacted any citizen facing services, Incident Manager will inform Senior Management of the pertinent details. You can find them in a collapsible row at the bottom of the list of fields. Learn how to create an Incident Response Plan >. Until the incident is resolved, these categories guide escalation. We will explore a list of the best Incident Management tools along with their features in this article. This posting does not necessarily represent Splunk’s position, strategies or opinion. Incident Management Support. Join this session to learn where ServiceNow Process Mining for HR fits in your digital transformation strategy and how you can start visualizing and seeing the reality of your business processes in minutes. Start your 14 day free trial.

Resources
NIRF 01 V12 Person Interactive. Sometimes, the incident is not easy, so you may also have to train the team members. Managing resources is the process of resource coordination during an occurrence. Automate your existing workflows with powerful Runbooks so you never have to manually run common tasks. Incidents in an IT environment can be categorized in several different ways. Fusion Framework System is a cloud based risk management and resilience platform that offers different solutions not just for risk management, but also for crisis and incident management, operational resilience, business continuity and disaster recovery. The Incident management process interfaces with various other Service management processes as shown in the diagram above. This way, your team won’t have to undergo the difficult process of resolving the same issue again. ServiceNow reports an issue when the company’s public website goes down.

Speed up work with intelligent bulk actions for tickets
With the fix implemented, the service desk team will then ask the end user if the fix is satisfactory and will close the incident. 3930 Fairview Industrial Drive SESalem, OR 97302. Now that you know what goes into an incident response plan, it’s time to create an incident log of your own. ITIL incident management is a reactive process. Dependency mapping tools can help illuminate how different components interact and may contribute to the incident. There are incident management getting started guides as well as Team Playbooks to educate your team on how to handle incidents. BankFodder posted a post in a topic, October 18. Compliance and audit trail. By classifying and prioritizing incidents effectively, you can ensure that the incident management team can focus on the most pressing issues first and allocate resources appropriately. It logs incidents by the instance, classifies them by level of impact and urgency, escalates as required and performs analysis for future improvements. An incident postmortem, also known as a post incident review, is the best way to work through what happened during an incident and capture lessons learned. Incident report prepared and submitted. The Steering Committee will meet one hour before each of the general meetings. Diagnosis may result in an update to the classification of the incident.

Resource utilization
Also, the San Storage Device can be checked. We hope that you have enjoyed the above article describing the ITIL Incident Management Process. XMatters increases your teams’ efficiency with the ServiceNow Major Incident plug in by. From these entry points, they can often proceed deep and unnoticed. It is important to take stock of the incident over a period of time to make sure it’s truly resolved. Agree and Join LinkedIn. With the help of a centralized incident management tool that follows Information Technology Infrastructure Library ITIL incident management protocol, ensuring function and security will be simple. Implementing recommendations for improvement. Regional, state and national incidents attract first responders from various local agencies. This reinforces the importance of setting up a MIM process that can effectively and efficiently tackle major incidents. Harsh Tandon is a Digital Marketing Lead at IFS assyst. By default, LogicMonitor will pre populate four different HTTP requests, one for each of. Through a peer based system, the Service seeks to offer employees the opportunity to meet with a trained Peer Support Member PSM who can provide support and assistance in developing a plan to deal with job related stressors and in problem solving personal issues before they become chronic and debilitating. You must perform attendance through multiple channels, the most used being telephone and internet interfaces, such as chats synchronous and e mails asynchronous. To further these objectives, agencies shall also consider opportunities to increase coordination, communication, and engagement about AI as appropriate with community based organizations; civil rights and civil liberties organizations; academic institutions; industry; State, local, Tribal, and territorial governments; and other stakeholders. Integrating Jira Service Management with Opsgenie is a one time action that will let the two applications exchange information between one another. A motor claim can at times be a very distressing experience. In other words, incidents are the nasty episodes on call employees are typically scrambling to resolve as quickly and completely as possible. This not only means you can help reduce the risk of violating SLAs, but also helps ensure your resolutions lead to happy end users. With VMware Cross Cloud services, you can address cloud chaos and shift to a cloud smart approach – one where you can choose the best environment for every application, without multiplying your complexity. Equipment can also get in the way when determining whether an incident is actionable, how severe it is, and how to prioritize it accordingly.

Incident response
Without incident management, handling tickets can be a hassle. A lower MTTD indicates a more effective incident detection mechanism. These are the ITIL Incident Management sub processes and their process objectives. Learn how to succeed in your role as a service project agent. Application Performance Monitoring APM. Fortunately, it seems the rest were well executed. Did you find it helpful. Priority is a combination of an Incident’s impact on the organization as well as its urgency level. Can my team pull in data and content from my other incident tools. Learn how to add the major incidents field and how to mark an incident major.
Security clearance
Don’t let your software limit what’s possible. 5 min read As organizations collect larger data sets with potential insights into business activity, detecting anomalous data, or outliers in these data sets, is essential in discovering inefficiencies, rare events, the root cause of issues, or opportunities for operational improvements. It will be used in concert with current SERT Operational Procedures. For example, users can find the answers to their own problems by performing a simple search without having to wait for a technician to get back to them. The prescribed processes help teams track incidents and actions in a consistent manner, which improves reporting and analysis, and can lead to a healthier service and a more successful team. Users like its intuitive UI and customizability. It’s not really possible to over communicate, so make sure to keep all the relevant stakeholders updated as you’re guiding your incident to resolution. Let’s learn more about the five steps of an effective incident management system, how to spot and resolve issues when they arise, and how resource allocation comes into the mix. This allows the service desk to analyze the incident and look for patterns, which could be instrumental in preventing future incidents. For example, its alert clustering algorithm groups related alerts together, minimizing noise and improving situational awareness. It’s basically an umbrella term for all the activities an IT team does to manage and improve the end to end delivery of its IT services to customers in order to meet business objectives. Incident management is the practice of responding to an unplanned event or service interruption and restoring the service to its operational state. By breaking the process down into clear steps, your team will be able to run diagnostics more efficiently and resolve faster. Some factors that influence incident categorization include the urgency of the incident and the severity of its impact on users or the business in general. They help provide valuable insights for improving incident response processes.
Stage 4: Maintenance
These processes take care of functions such as optimization of facility management, automation of emergency response, and more — all of which relate to incident management. Prioritization and Linkage to CI. What does incident management look like in action. Apart from chat platforms, any powerful conference bridge like Zoom, Teams, Webex etc. The ICS Command Staff typically includes. Also, make sure the service desk has updated the welcome message on their Automatic Call Distribution ACD system to try and stop the avalanche of calls. They show no hesitation in delegating tasks to anyone. To close the incident, the incident owner should verify with the person who reported the incident that the resolution is satisfactory. This leads to the question of who reports an incident and how. With great organization features, everything is within arm’s reach. This can reveal potential points of failure or bottlenecks, such as a slow database server or issues with the payment gateway service, allowing the incident management team to investigate and resolve the incident more effectively. Incident response explained. If a temporary workaround is in place, once the disruption to end users is mitigated, IT staff can develop a long term fix for the issue. ClickUp is a project management tool, but teams can use it to manage and respond to incidents. Incident management for organizations must be largely proactive. If you are preparing for the ICS 800 final exam in May, it is essential to study and be well prepared. Incident management software is a type of tool or system that is used to track and manage incidents or events that occur within an organization. Choosing the right instance offering and instance size for your application is critical for optimizing performance and reducing. Once a complaint is received, the service desk or other responsible party must identify whether it is a true incident or simply a request. For example, DevOps teams might monitor for poor mean time between failures MTBF metrics, which is a clear indication of an underlying issue that requires investigation. While AI technology offers immense potential for businesses, it also presents risks and requires governance. The goal is to keep systems online and operational, whether apps or endpoints such as sensors or desktop computers. Package also include Preventative Measures which are important information for establishment of Problem Management and Root Cause analysis. This intuitive, cloud based solution empowers teams to collaborate in real time to build flowcharts, mockups, UML diagrams, customer journey maps, and more. First developed for use with military combat veterans and then civilian first responders police, fire, ambulance, emergency workers and disaster rescuers, it has now been adapted and used virtually everywhere there is a need to address traumatic impact in people’s lives. And it’s not just the financial loss. Define how the organization will identify and eradicate all components of the root cause of the contained security incident, then define how the organization will recover from the eradicated security incident. Here are some important KPIs to track major incident management. Our purpose is to make the experience as painless as possible by managing the vehicle through every step of the journey. It’s much better to focus on restoring the business process as the key incident management activity, and allow problem management to take whatever time it needs to do root cause analysis later.
Announcement number
These events, which include having to witness or experience tragedy, death, serious injuries and threatening situations are called “Critical Incidents. Can I visualize my infrastructure graphically. Out of these cookies, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities. Or submit a pull request and help us build better products for everyone. They have said the letter of value they sent 2 months ago reflected on the current market value if we had been paid out there and then is subject to change as time goes on. Automate incident response, keep your stakeholders informed, and reduce downtime. When the functioning of any activity becomes a failure and causes the system to act in an unplanned fashion, it is termed as an incident. It is good practice to implement the fix for the major incident as a change to ensure that the resolution is properly documented and implemented. Native features and numerous integrations ensure adaptability and support for specific team requirements, extending the software’s functionality as needed. Effective deployment is releasing a software application, system update, or any other type of code. We’ll pick X up once the immediate issue has been resolved. B testing and safeguards against discriminatory, misleading, inflammatory, unsafe, or deceptive outputs, as well as against producing child sexual abuse material and against producing non consensual intimate imagery of real individuals including intimate digital depictions of the body or body parts of an identifiable individual, for generative AI;. The service project automatically closes the incident. Page Technical Resources. As part of this process, it’s essential to coordinate response efforts and engage relevant stakeholders. WordPress® is a registered trademark. It can also include the measures you take to prepare your company to handle incidents in general—whether that’s a minor issue like a printer not printing or something far more serious, like a cyber attack. Why does incident management even matter in the first place. SolarWinds Service Desk puts your agents at the center of their work, from agent customizable incident overview screens, live agent collaboration on tickets, AI recommended fixes, and multi ticket resolution. VictorOps is an incident management tool designed with DevOps in mind. The categorization is an arrangement of the event type, such as the device, service, or location. You wish to learn more about SmartITSM.
Company
The key is to take intelligent risks and be decisive in the following steps. Incident management deals with individual incidents, while problem management takes a broader perspective to address systemic issues. NIRF 05 HCW COVID 19 Acquired V02 NIRF Interactive. Application Performance Monitoring APM. It makes sense: inbound queries should always be routed to the best available servers—usually the ones that are geographically closest. The classic incident management activities as outlined in ITIL 4 are seen below. It offers a straightforward network monitoring software that provides real time updates and alerts. Even if a debt has been to court. MIMs typically make security related decisions, oversee the response process and allocate tasks internally to facilitate our response process. This allows them to quickly respond to disruptions, get up to speed with what’s going on, create incidents and provide more context for the Opsgenie teams to resolve them. Incident Management, Case Studies. Assign to support Analyst. Unfortunately, many organizations also have manual processes for managing incidents that are challenged to keep up with fast paced, agile methodologies or hybrid cloud environments. The templates require extensible attributes described in the table below. Adam Blevins, CCISM, Operations Director; Virginia Law Enforcement Assistance Program. Copyrights ©2023 Muvi. Picture a well oiled machine smoothly navigating the challenges presented to business operations by unexpected incidents. Here’s a 6 step process to approach incident management. The following ITIL terms and acronyms information objects are used in the ITIL Incident Management process to represent process outputs and inputs. There’s nothing worse than being blindsided by an angry customer, so make sure anyone dealing with escalations knows what’s going on, the current status, and any plans in place to fix the issue. 580 As a Restaurant Manager atSteak ‘n Shake, you’ll: Effectively manage a Steak ‘n Shake Shift; Execute the14 point walk and correct deficiencies as they arise; Ensure food is properlystored and. The solution ingests and aggregates incident alerts and integrates with monitoring systems. Open this template to view a detailed example of an incident management process flow that you can customize to your use case. Not only will an ITIL incident management platform serve as an incident tracker and incident report software, but it can also offer analysis and reporting capabilities that make resolving issues easier. A detailed major incident management procedure is your best guardian angel and can be a lifesaver in these situations. Headed to an interview. Here are some of the compelling benefits of having an incident management process –.
Versions
Your course materials include a “Setup Instructions” document that details important steps you must take before you travel to a live class event or start an online class. Major incidents may need significant recovery efforts. Incidents can be spotted through user alerts, infrastructure metrics, or unusual behavior detection. Most likely, the answers to these questions will not be optimal, as most companies fall short in one area or more, according to a study by the Ponemon Institute. A problem is an underlying cause of the incident. Home IT Service Management Software. The review process will be used to identify requirements for new or changed policies, to update the University risk register and to identify any other relevant controls. Successful incident management relies on having a clear understanding of what the customer agreed to or is willing to tolerate regarding the duration and handling of any particular incident. Tier I teams perform the initial analysis and investigation. For major incidents, the domino effect of outages can have a major impact on the business and the stakeholders involved. Properly prioritizing incidents also allows you to avoid costly downtime, which frustrates users, IT, business leaders—pretty much everyone in the company, come to think of it. Service outages can be costly to the business and teams need an efficient way to respond to and resolve these issues quickly. To link multiple incidents to a problem report. If you feel like more information should be added to your response log but there isn’t enough room, consider linking to an outside space or document where more detailed responses live. DSO IFZA Properties, Dubai Silicon Oasis, Industrial Area, Dubai, United Arab Emirates 341041. This ticket includes information such as the user’s name and contact information, a description of the incident, and date and time of the initial log. This may happen for several reasons as discussed in Section 5 – Response escalation guidelines. By configuring an automation rule in advance, IT teams can have tickets automatically closed based on certain conditions without investing the manual effort. This diagram depicts how Incident Management is operated and the interfaces associated with it. They can range from the whole service crashing to intermittent errors that concern only a small number of users. After an event is identified as an incident, it is logged in the next step of the Incident Management Process. It limits unnecessary costs by avoiding worker’s compensation and property damage claims, environmental clean up costs and insurance premium hikes. On call teams are rapidly evolving. Jira Service Management. I issue a public report describing the potential for AI to improve planning, permitting, investment, and operations for electric grid infrastructure and to enable the provision of clean, affordable, reliable, resilient, and secure electric power to all Americans;. When system errors prevent network functionality, your employees will be uneasy about the privacy and quality of their work environment. By clicking Continue, you agree to LinkedIn’s User Agreement, Privacy Policy, and Cookie Policy. Fusion integrates with Onsolve, EveryBridge, AlertMedia, ServiceNOW, and other emergency notification systems, configuration management databases, and situational intelligence platforms. Get the latest news, announcements, views, and more.
Simas Stasenis
The incident management process can be summarized as follows. Pagerduty is the oldest provider of incident management and has all the capabilities people could want. Resolution tasks executed. Want to see how Atlassian handles major incidents. The next stage in incident management is incident categorization and prioritization. The catalyst for incident management is when an end user, monitoring system, or IT specialist reports an interruption. Good e Learning is an award winning online training provider, as well as an accredited Market Leader for ITIL training. A definition of what constitutes a major incident must be agreed and ideally mapped onto the overall incident prioritization scheme – such that they will be dealt with through this separate procedure. Typical use of ITS devices and the roles and responsibilities of the TCC and Mobile Safety Service Patrols are summarised in the two tables below for different stages of an incident. In this insightful webinar session we would cover the importance of SSO in access management, aligning multi factor authentication MFA and also explore user/device policies. This is not always easy in a fast moving emergency situation and requires a high level of awareness and responsiveness to their own internal state and also the needs of team members. Incident Resolution by 2nd Level Support. They can even be raised without the existence of a corresponding incident. A procedure should be in place to manage all aspects of a major incident, including resources and communication. Once the incident has been identified, it should be logged by the service desk. This is particularly important if it is a major incident that requires an urgent response. Having a robust incident response program can be the difference between sinking and swimming. This may include temporarily incorporating staff or management from the department into the Incident Response Team. E independent evaluation of vendors’ claims concerning both the effectiveness and risk mitigation of their AI offerings;. Virginia law enforcement officers, dispatchers and members of Virginia police CISM/peer teams may attend this training at no cost. It goes Incident > Problem > Change. An Incident Management Plan ensures customer satisfaction through quick and efficient response, analysis, and logging of an incident. SysAid’s built in remote control capabilities allow service desk agents and other IT support personnel to connect to end user active sessions, or unattended computers, to give remote assistance. Saved in engineering hours. First, you have to identify potential IT incidents.